What Is a Windows VPS? A Complete Guide for R
What Is a Windows VPS? A Windows VPS (Virtual Privat...






In late January 2026, the VPS and cloud hosting community was shaken by a serious security incident involving CloudCone’s Los Angeles VPS infrastructure. Multiple customers reported sudden service failures, corrupted boot sectors, and unrecoverable data loss. Shortly afterward, CloudCone officially confirmed that a subset of their Los Angeles VPS nodes had been compromised.
The root cause was traced back to a Virtualizor-related vulnerability or attack vector, once again placing third-party virtualization management panels under intense scrutiny.
https://lowendtalk.com/discussion/214073/what-happened-to-cloudcone-was-it-hacked
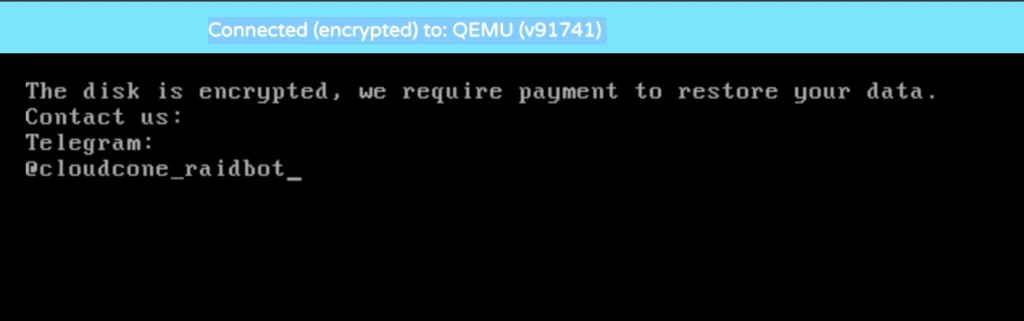
This incident is not just about CloudCone. It serves as a broader warning for the entire hosting industry: control panel security is infrastructure security. In this article, we will examine what happened, why Virtualizor-based environments have become high-value targets, and why self-developed cloud management platforms—such as SurferCloud—are increasingly seen as the safer long-term approach.
Around January 29–30, 2026, CloudCone customers using Los Angeles VPS nodes began experiencing:
Soon after, CloudCone released an incident notice acknowledging:
While CloudCone did not initially disclose every technical detail, subsequent community discussions and internal updates pointed to Virtualizor, the virtualization management panel used for their VPS platform, as the attack surface.
Attackers allegedly exploited panel-level access paths—possibly involving terminal or node management functions—to execute destructive commands at the host or storage layer.
The result was catastrophic for affected users: even snapshots and standard recovery methods were rendered useless.
Virtualizor is widely used across the VPS market, especially among small and mid-sized hosting providers. While powerful and feature-rich, it also introduces systemic risk.
When thousands of providers use the same management panel, attackers can:
This creates a “single point of failure” problem at an industry level.
Virtualizor operates with deep host-level permissions:
If attackers gain access to panel-level functions, they are effectively inside the hypervisor environment, not just a single VPS.
Even when vulnerabilities are disclosed:
This creates long exploitation windows.
For end users, the CloudCone incident highlights several uncomfortable truths:
Many affected users learned—painfully—that infrastructure-level incidents are fundamentally different from:
When the control plane is compromised, everything above it collapses.
This incident reignited a long-running debate in the hosting industry.
Pros
Cons
Pros
Cons
In recent years, more serious cloud providers have chosen the second path.
SurferCloud does not use Virtualizor or other third-party VPS panels.
Instead, SurferCloud operates on a fully self-developed cloud server management and control platform, covering:
This design significantly reduces exposure to mass-exploitable panel vulnerabilities.
Because SurferCloud controls the entire stack:
This is the same philosophy used by major cloud providers like AWS, GCP, and Azure.
Another lesson from the CloudCone incident is the importance of isolation and transparency.
SurferCloud emphasizes:
Even in worst-case scenarios, this architecture is designed to prevent cross-node catastrophic failure.
If you are:
Then the difference between a panel-based VPS and a cloud-native platform is not academic—it is existential.
Downtime is painful.
Total data loss is fatal.
The CloudCone incident will not be the last control-panel-related security event. But it will likely accelerate existing trends:
SurferCloud represents this next stage of VPS and cloud evolution: less reliance on shared tooling, more ownership of the control plane.
The CloudCone Los Angeles VPS incident is a reminder that:
In cloud infrastructure, the control panel is as critical as the hypervisor itself.
While third-party virtualization panels have powered the growth of affordable VPS hosting, they also introduce systemic risks that become more apparent with each large-scale incident.
For users who prioritize long-term stability, security, and architectural maturity, platforms like SurferCloud, built on self-developed cloud management systems, offer a compelling alternative.
Security is not a feature—it is a foundation.
What Is a Windows VPS? A Windows VPS (Virtual Privat...
Common Problems With Big Vendors AWS, Azure, Google ...
CentOS VPS hosting is a top choice for developers, busi...