Google Chrome Remote Desktop Beginner Guide 2
Remote desktop software has become a daily tool for dev...







APIs are the backbone of cloud services, but they can also be a major security risk if not properly tested. Here's why API penetration testing is critical for protecting cloud hosting platforms:
Recognizing vulnerabilities in cloud APIs is essential for implementing effective penetration testing to safeguard these secure cloud infrastructure environments.
Cloud APIs are exposed to unique vulnerabilities that differ from those found in traditional web applications. One of the most critical issues is Broken Object Level Authorization (BOLA). This occurs when an API fails to verify whether an authenticated user has permission to access a specific object ID. Attackers exploit this by modifying object IDs to gain unauthorized access to sensitive data [4].
Broken Authentication is another frequent issue. APIs that rely on predictable tokens, lack multi-factor authentication, or use weak credential validation mechanisms are vulnerable to account takeovers and credential stuffing attacks. Dan Barahona from APIsec has emphasized that most API breaches are rooted in authorization oversights [2].
Unrestricted Resource Consumption is a risk where attackers flood the system with excessive requests, depleting resources and potentially causing denial-of-service conditions or increased operational costs. Choosing the right elastic compute or application server configuration can help mitigate some of these infrastructure-level risks. Similarly, Server-Side Request Forgery (SSRF) can occur when an API retrieves remote resources without validating the supplied URI. This opens the door for attackers to access internal networks or cloud metadata services. Another concern is Improper Inventory Management, which can result in "shadow" APIs - undocumented endpoints that lack proper security measures and often go unnoticed.
In fact, nearly all organizations have reported at least one API security issue within a 12-month period. Authorization flaws and business logic vulnerabilities consistently emerge as the most exploited patterns in real-world attacks [4][2].
These vulnerabilities highlight the need for targeted, manual testing to uncover hidden risks that automated tools might miss.
Real-world breaches serve as stark reminders of these vulnerabilities. For example, in January 2025, a security researcher at Vorlon discovered a major flaw involving a third-party vendor's public Postman workspace. This workspace exposed valid credentials to an athletic brand's Okta IAM system, putting sensitive data such as invoices, shipment details, and trade secrets at risk. Alarmingly, over 30,000 public Postman collections were similarly compromised [5].
These incidents demonstrate the limitations of automated scanners, which often fail to detect context-dependent flaws, especially those related to authorization. This underscores the importance of manual penetration testing to identify these nuanced vulnerabilities and prevent severe breaches.
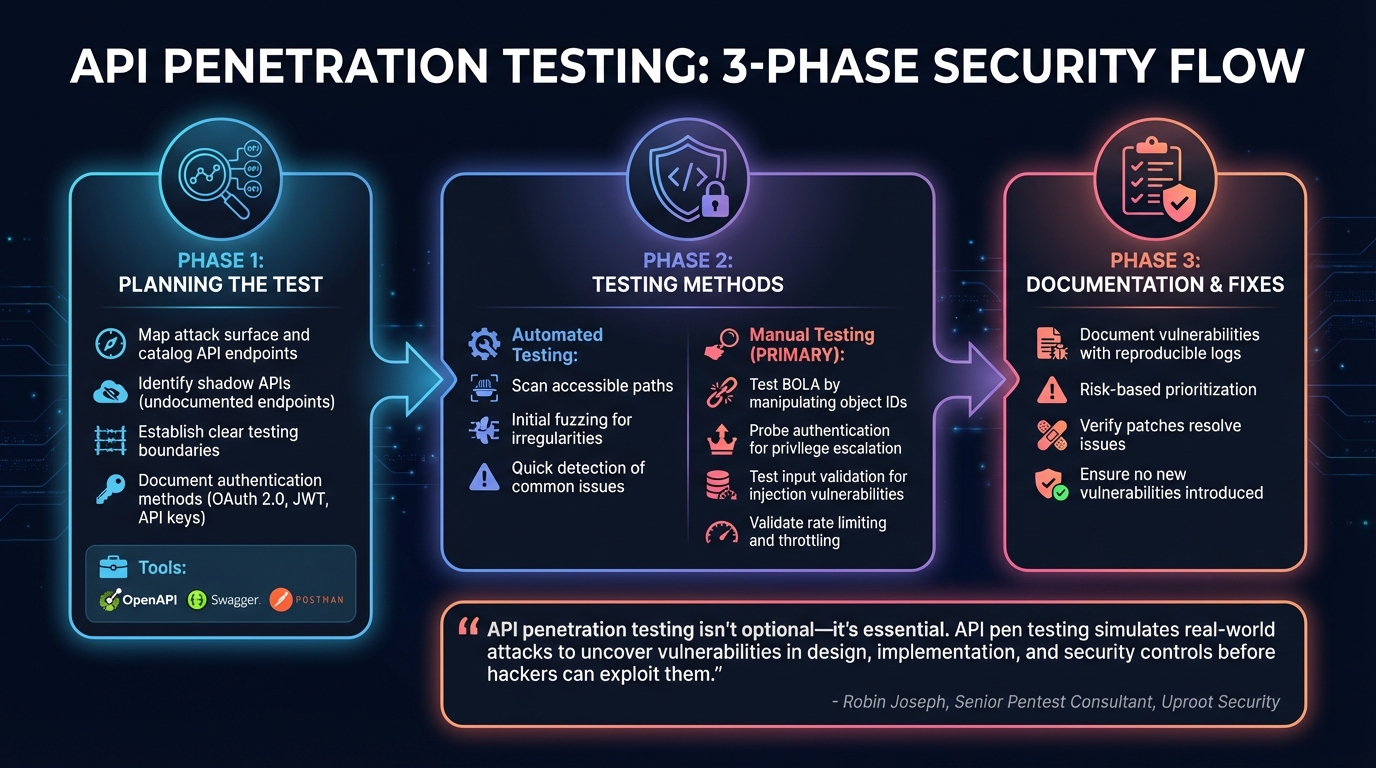
API Penetration Testing Process: 3-Phase Security Workflow
API penetration testing mimics real-world attacks on cloud systems to uncover vulnerabilities and strengthen security. With the many API weaknesses previously discussed, this type of testing plays a key role in safeguarding cloud services. It combines automated tools with hands-on analysis to pinpoint flaws that could expose sensitive data or disrupt operations. By addressing known vulnerabilities, this process helps reinforce the overall security of cloud environments.
The first step is to map out the attack surface, which involves cataloging all API endpoints. Tools like OpenAPI, Swagger, and Postman are commonly used for this. Testers also hunt for shadow APIs - undocumented endpoints that might bypass security measures.
Establishing clear boundaries is crucial. Teams decide which endpoints are included in the test, set limits to avoid unintentional outages, and exclude certain systems, such as production databases. They also outline the authentication methods in use - whether it’s OAuth 2.0, JWT tokens, or API keys - and document how credentials are handled and transmitted.
Once the endpoints are mapped, testers use both automated and manual methods to evaluate security. Automated tools scan accessible paths and perform initial fuzzing to detect irregularities. These tools help identify common issues quickly.
However, manual testing is where deeper, context-specific flaws often come to light. Testers focus on business logic vulnerabilities by manipulating object IDs to uncover Broken Object Level Authorization (BOLA) issues or testing low-privilege access for Broken Function Level Authorization (BFLA). Authentication mechanisms are probed for weaknesses like privilege escalation, token reuse, or bypassing identity verification. Input validation is rigorously tested for injection vulnerabilities, including SQL, command, or JSON payloads. Additionally, resilience is checked by validating rate limiting and throttling mechanisms to guard against denial-of-service attacks.
"API penetration testing isn't optional - it's essential. API pen testing simulates real-world attacks to uncover vulnerabilities in design, implementation, and security controls before hackers can exploit them." - Robin Joseph, Senior Pentest Consultant, Uproot Security [6]
Every vulnerability discovered is thoroughly documented, complete with reproducible logs and a risk-based prioritization. Once fixes are applied, testers verify that the patches not only resolve the issues but also don’t introduce new vulnerabilities, ensuring a more secure system overall.
API penetration testing plays a key role in preventing breaches by identifying vulnerabilities that attackers could exploit. In the United States, the average cost of a data breach is projected to hit $10.22 million per incident by 2025 [1]. By simulating attacks, this testing ensures that critical security measures - like rate limiting, input validation, and access controls - are functioning as intended. It also uncovers complex flaws that automated scans often miss, such as when authenticated users manipulate request parameters to gain unauthorized access to data [2]. Fixing these issues not only prevents financial losses but also helps avoid fines and keeps operations running smoothly.
Beyond mitigating risks, API penetration testing is essential for meeting compliance standards. Regulations like GDPR, PCI DSS, and HIPAA require secure handling of sensitive data, including personal information, payment details, and medical records [6][8]. The NIST SP 800-228 guidelines, introduced in June 2025, specifically highlight the importance of securing APIs in cloud-native systems by identifying risks throughout their lifecycle [3]. Regular testing demonstrates accountability, helps align with ISO 27001 standards, and is a crucial step in obtaining FedRAMP authorization for federal agencies using cloud services [9].
Protecting customer data is not just about security - it’s about trust. Comprehensive API penetration testing reassures customers that their sensitive information, whether it's PII, payment data, or medical records, is being actively safeguarded. This proactive approach also minimizes downtime and revenue losses caused by API-related attacks, ensuring smoother business operations. For development teams, it provides the confidence to roll out updates knowing that endpoints are secure and reliable.
At SurferCloud, we take penetration testing seriously to protect sensitive data and maintain the resilience of our cloud infrastructure. This commitment strengthens customer trust and ensures their information is consistently safeguarded.
This case study highlights how focused API penetration testing can address and resolve vulnerabilities that put sensitive data at risk.
In November 2021, an arts and entertainment company uncovered serious security flaws in their website after working with the Cisco Talos Incident Response Red Team. Their public-facing APIs lacked proper authorization controls, which left customer data exposed. This gap allowed unauthorized access to loyalty cards and credit card tokens [10]. Testers were able to view private user profiles containing details like phone numbers and birthdates. Even worse, they could exploit credit card tokens to make purchases without any verification.
Using standard penetration testing techniques, the team thoroughly mapped the API attack surface and pinpointed critical security weaknesses. While authentication was in place, there was no authorization system to regulate access. This loophole allowed testers to manipulate object IDs and retrieve entire database objects [2]. By altering API object IDs, they gained access to sensitive user profiles and transaction data. These vulnerabilities, a classic example of Broken Object Level Authorization (BOLA) [2], severely compromised the API's security. The discoveries underscored the need for immediate and decisive action to protect the company's data.
Following the testing phase, the company took swift measures to strengthen its API security. They restricted external API access, implemented role-based permissions, revoked active tokens, and updated their vulnerable web servers [10]. These steps significantly improved their security framework, effectively safeguarding their cloud ecosystem. By addressing these vulnerabilities, the company transformed its API security from a major liability to a robust defense, preventing unauthorized data access and fraudulent activities.
API penetration testing has become an essential part of modern security practices, far beyond being just a regulatory requirement [6]. With APIs now handling over 80% of web traffic and nearly 40% of data breaches traced back to insecure endpoints [7], organizations must prioritize API security. High-profile breaches, such as those affecting T-Mobile and Optus, highlight how vulnerabilities exposing millions of customer records can be identified and fixed before attackers take advantage [2].
The most effective approach combines automated tools for initial assessments with manual testing to uncover deeper flaws, especially those tied to complex business logic [4, 11]. Incorporating API penetration testing into DevSecOps workflows, conducting tests before major releases, and maintaining an up-to-date inventory of all endpoints - including shadow APIs - are critical steps [2, 4]. This integrated strategy not only strengthens security but also boosts trust among stakeholders.
Regular testing does more than just prevent breaches; it builds customer confidence and operational resilience. With the financial toll of data breaches continuing to rise, proactive measures like penetration testing protect sensitive information and ensure uninterrupted service.
"API penetration testing isn't just another security checkbox - it's an investment in the resilience and trustworthiness of your organization" [6].
As threats evolve, so must defenses. Emerging technologies like zero-trust architecture and AI-driven security are enhancing the sophistication of API testing. Organizations that adopt a consistent testing routine will be better equipped to counter new risks while staying compliant with regulations like GDPR, HIPAA, and PCI DSS [3, 11].
These proactive measures are vital for securing cloud environments. At SurferCloud, we understand the importance of staying ahead of threats. By rigorously testing our APIs, we ensure that our secure, scalable, and high-performance cloud solutions remain resilient against the ever-changing threat landscape.
Manual API testing plays a crucial role in ensuring security because it closely replicates real-world attack methods. This process uncovers business logic flaws, configuration errors, and other vulnerabilities that automated tools might miss. By taking this hands-on approach, you can verify that your cloud API security measures are not just implemented but are genuinely effective against potential threats.
Through manual testing, you can gain a clearer understanding of your system's weak points. This allows you to address risks that could lead to data breaches or service interruptions, making it an essential step toward creating a secure and resilient cloud environment.
Shadow APIs refer to API endpoints that are neither documented nor actively managed by an organization. These endpoints often come into existence unintentionally - perhaps through developer actions or third-party integrations - and typically fall outside the scope of the company’s official security oversight.
The lack of visibility around shadow APIs makes them risky. They can expose sensitive data, remain vulnerable due to unpatched security flaws, and serve as entry points for attackers. This creates opportunities for malicious actors to bypass defenses and access critical systems or information undetected.
API penetration testing plays a critical role in helping organizations align with regulatory standards such as GDPR, PCI DSS, NYDFS, and HIPAA. By mimicking potential attacks, it uncovers vulnerabilities like misconfigurations, broken authorization mechanisms, and logic errors, all of which could lead to data breaches. Detailed reports from these tests not only highlight issues but also document remediation efforts, showcasing due diligence to auditors and regulators.
Take PCI DSS as an example - it requires safeguarding cardholder data against unauthorized access. API penetration testing ensures that endpoints enforce proper authentication and authorization, providing the evidence needed for compliance. Similarly, GDPR requires robust technical measures to protect personal data. Test reports from penetration testing serve as proof that APIs managing sensitive information are secure and meet these requirements.
SurferCloud customers gain an added layer of security by incorporating API penetration testing into their cloud service lifecycle. This approach ensures compliance while enhancing the security and reliability of services like compute, storage, and networking. The detailed reports generated can be shared with auditors and regulators, reducing risks and strengthening trust in SurferCloud's secure infrastructure.
Remote desktop software has become a daily tool for dev...

Hybrid cloud architecture combines on-premises systems ...
The rise of Web3 is transforming how applications, game...