SurferCloud: A Reliable and Customer-Centric
Selecting the right cloud hosting provider is essential...







Managing multi-cloud networks is complex, but policy-driven automation simplifies it by centralizing configurations, compliance, and operations across platforms like AWS, Azure, and GCP. This approach ensures consistency, reduces manual errors, and enhances security in increasingly dynamic cloud environments.
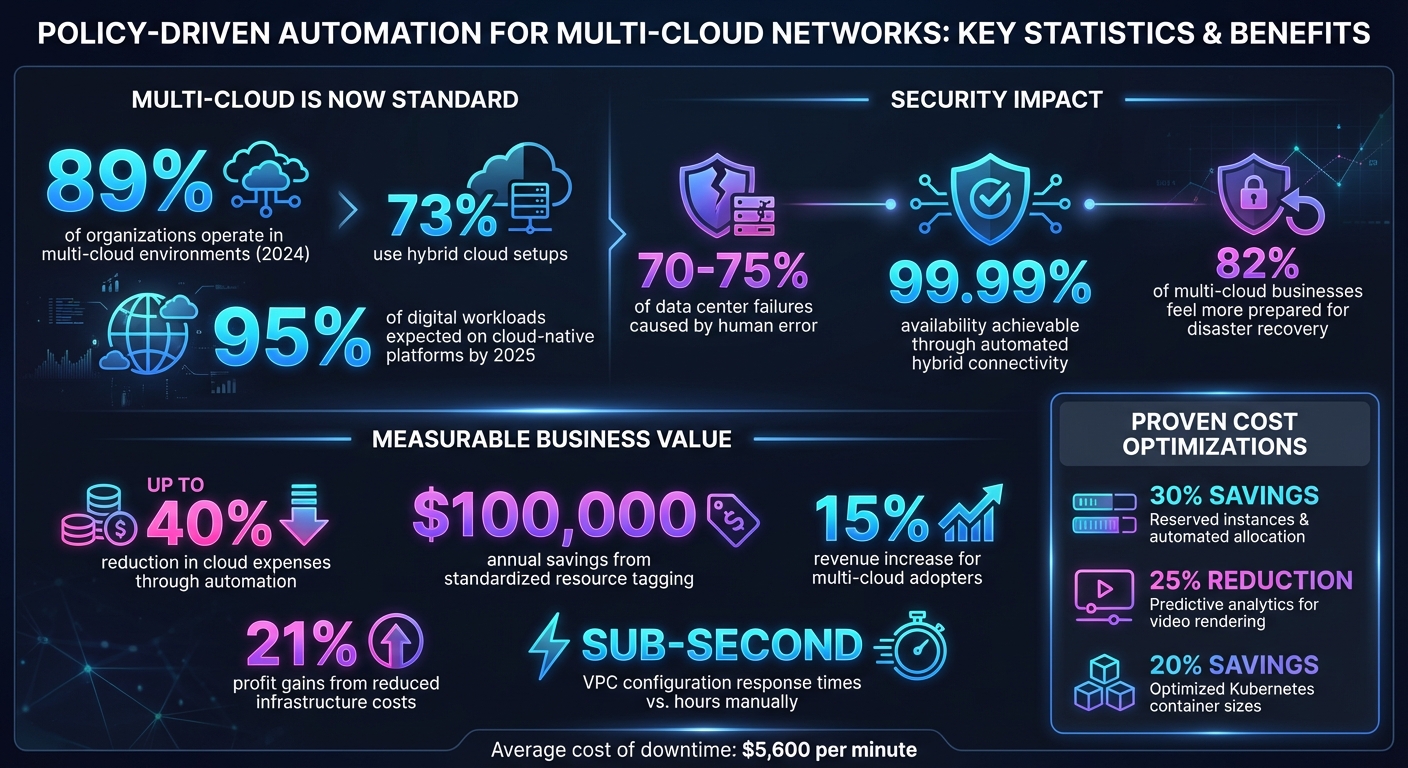
With 95% of digital workloads expected to run on cloud-native platforms by 2025, adopting automation isn’t optional - it’s essential for maintaining agility, security, and cost efficiency.
Policy-Driven Automation Benefits: Security, Cost Savings, and Multi-Cloud Adoption Statistics
Policy-driven automation in multi-cloud networks relies on three key technologies: centralized policy management frameworks, intent-based networking with SDN integration, and orchestration tools. These technologies work together to translate business needs into automated configurations.
Centralized frameworks offer a single point of control for defining and enforcing policies across various cloud environments. Instead of juggling multiple logins, teams can manage everything from one interface. A great example of this is the Cisco Application Policy Infrastructure Controller (APIC), which transforms logical policy models into executable configurations [8]. It maintains a full representation of both administrative and operational states, ensuring that changes are applied to the policy model before being pushed to endpoints [8][9].
Another tool, Cisco Identity Services Engine (ISE), enhances standardization by sharing Security Group Tags (SGTs) across platforms like ACI, SD-WAN, and public cloud providers [4]. These frameworks decouple logical configurations from physical hardware, enabling workloads to move freely without requiring manual adjustments [8][9].
This centralized control lays the groundwork for intent-based networking, which focuses on achieving specific outcomes rather than manual configurations.
Intent-Based Networking (IBN) shifts the focus from "how" to configure devices to "what" outcomes the network should deliver. As described in RFC 9315:
Intent is a set of operational goals (that a network should meet) and outcomes (that a network is supposed to deliver) defined in a declarative manner without specifying how to achieve or implement them [10].
SDN controllers play a crucial role here, converting high-level policies into detailed instructions like VLAN allocations and routing rules [8]. Cisco's ACI fabric, for example, ensures consistent low-latency forwarding over high-bandwidth connections, supporting speeds of 40 Gbps and even 100 Gbps [8].
Once the desired outcomes are defined, orchestration tools step in to automate the operational processes.
Orchestration platforms are essential for automating the infrastructure lifecycle. For instance, Juniper Contrail Enterprise Multicloud leverages BGP EVPN/VXLAN standards to create overlay networks that link physical and virtual endpoints across multiple clouds [12][15]. Its vRouter technology acts as a virtual gateway for public cloud VPCs, providing a consistent data plane for both virtual machines and containers [15].
On the other hand, AWS Cloud WAN uses Core Network Policy (CNP), a single versioned document that defines segments and routing domains across VPCs and on-premises environments [13]. Meanwhile, ONAP (Open Network Automation Platform) offers a modular setup, where components like the Service Orchestrator manage workflows, and the Software Defined Network Controller handles network coordination [14]. Over time, ONAP has evolved into a more flexible model, allowing organizations to integrate only the functions they need [14].
VXLAN technology underpins these orchestration tools, efficiently managing multi-cloud integrations [7]. Standard APIs like REST, NETCONF, and gRPC enable seamless interoperability [15]. At SurferCloud, integrated orchestration tools ensure smooth policy enforcement across our 17+ global data centers, eliminating the need for manual intervention.
Using centralized management and orchestration tools, policy-driven automation simplifies operations while delivering measurable advantages. These benefits directly address common challenges and result in improved security, cost savings, and scalability. For organizations managing multi-cloud networks, these improvements translate into financial benefits and reduced risks.
Centralized enforcement helps eliminate security gaps caused by manual configurations. By defining a security policy once and applying it consistently across platforms like AWS, Azure, and GCP, organizations achieve uniform protection without relying on provider-specific tools [2]. This approach is crucial because human error accounts for 70% to 75% of data center failures [22], with misconfigurations being a leading cause of cloud security breaches.
Automation also supports a shift to identity-based security. As outlined in NIST SP 800-207A:
One of the basic tenets of zero trust is to remove the implicit trust in users, services, and devices based only on their network location, affiliation, and ownership [6].
Tools such as SPIFFE and sidecar proxies enforce detailed application-level policies, regardless of where workloads are hosted [6]. For industries with strict compliance requirements, automated platforms continuously monitor adherence to standards like CIS Benchmarks, NIST, PCI-DSS, and GDPR, providing account-level compliance scores [5]. Organizations can also achieve 99.99% availability for hybrid connectivity through automated, redundant interconnect connections [11].
Automation minimizes overhead by streamlining configurations and preventing resource waste. For example, organizations using reserved instances and automated resource allocation have reduced cloud costs by 30%. Standardized resource tagging has generated annual savings of $100,000 by improving cost visibility [16]. Predictive analytics for tasks like video rendering can lower costs by 25%, while optimizing container sizes in Kubernetes environments reduces cloud expenses by 20% [16].
Centralized management also consolidates billing data, enabling precise cost forecasting and real-time scaling [5]. Auto-scaling ensures infrastructure adapts to traffic demands, so organizations pay only for the resources they use [2]. Additionally, placing automated gateways closer to applications reduces data transfer and egress costs [2]. By locking in lower rates for predictable workloads through reserved instances, companies can save up to 40% compared to on-demand pricing [16].
These efficiencies directly support the scalability and flexibility of network operations.
Policy-driven automation allows businesses to grow their cloud environments without significantly increasing administrative workloads. As of 2024, 89% of organizations operate in multi-cloud environments, and 73% use hybrid cloud setups [18]. Embedding policies into CI/CD pipelines ensures governance remains strong as networks expand [17]. Deployment templates like Terraform or ARM enable quick, consistent setups by applying preset security and compliance configurations across environments [17].
Automation is the backbone of effective multi-cloud governance. By integrating policies directly into CI/CD pipelines, businesses can grow without increasing administrative workloads.
Vendor-neutral architectures using open-source tools like Kubernetes provide flexibility to migrate and optimize applications across multiple providers without being locked into proprietary systems [18][20]. This approach allows organizations to combine specialized services - such as AI tools from one provider and compute resources from another - to create tailored infrastructures [19][21]. Automated governance policies further enhance efficiency by shutting down unused resources or reallocating workloads to cost-effective providers [18]. With the average cost of downtime reaching $5,600 per minute, these measures are critical for maintaining a lean and adaptable network [21].
Configuring cloud networks manually is a time-intensive task that requires specialized expertise, particularly when dealing with large-scale topologies. Automation frameworks like AutoNet have demonstrated impressive efficiency, achieving sub-second response times for generating Virtual Private Cloud (VPC) configurations in production environments - an enormous improvement over traditional manual methods [1]. Additionally, advanced tools using MaxSAT encoding and Binary Decision Diagrams have made it possible to scale policy management to thousands of nodes [1].
The transition from reactive to proactive management has introduced a transformative approach. While traditional tools often identify bugs after they've caused issues, policy-driven automation mitigates misconfigurations before they occur [1]. This proactive strategy highlights the interconnectedness of network configurations, where even small, localized changes can ripple across the entire system. These advancements have paved the way for practical applications in various industries.
In the financial sector, organizations rely on policy-driven automation to uphold PCI DSS and SOC2 Type2 compliance by implementing unified security controls and Data Loss Prevention (DLP) mechanisms to protect Personally Identifiable Information (PII) [2][4]. Many financial institutions adopt "Common Policy" architectures, which share contextual data about users and devices across domains. This enables precise enforcement, such as allowing employees access to internal web apps while restricting contractors to specific cloud-based tools [4].
E-commerce businesses, on the other hand, benefit from auto-scaling gateways that dynamically adjust to traffic spikes, ensuring consistent protection through web application firewalls (WAF) and defense against denial-of-service (DoS) attacks [2]. Automated segmentation further safeguards these environments by preventing lateral threat movement within multi-cloud setups - a critical measure for securing sensitive financial transaction data [2]. By separating the control plane from the data plane, companies can define a single policy and implement it seamlessly across platforms like AWS, Azure, GCP, and OCI, significantly reducing operational complexity [2][23].
Organizations use a variety of metrics to assess the success of automation efforts.
Scalability is another critical benchmark. For example, Cisco ACI, integrated with ISE, supports up to 64,000 combined IPv4 and IPv6 IP-SGT bindings and 32,000 endpoints per fabric [4]. High-performance multi-cloud gateways also deliver throughput in the range of multiple Gbps per instance while performing deep packet inspection [2]. These metrics underscore the importance of adopting strategic, policy-driven approaches, setting the stage for the implementation guidelines discussed next.
When implementing policy-driven automation, it's essential to separate decision-making from enforcement. Using tools like Open Policy Agent (OPA) allows you to isolate policy logic from your infrastructure, ensuring consistent enforcement across environments like microservices, Kubernetes clusters, and CI/CD pipelines [25]. This setup means you can adjust security rules or regulatory requirements without touching your application code.
A hierarchical approach to policies is also key. By setting up policy tiers, you can enforce strict security measures while still allowing flexibility for application-specific rules [26]. For instance, your security team could enforce a global "zero trust" policy that blocks all traffic by default, while application teams define specific connectivity rules for their namespaces [26].
In cloud-native environments, unique label schemas are crucial for effective policy enforcement. Unlike traditional networks that rely on static IPs, multi-cloud setups use labels and selectors to identify resources. For example, using labels like app: payment-gateway can reduce CPU and memory usage [26][5].
Adopting a Policy-as-Code approach is another best practice. This means treating policies like software - building, testing, version-controlling, and deploying them automatically [24][26]. For instance, instead of embedding CIDRs or domain names into individual policies, you can use "network sets" to group IP addresses and subnets. This method improves scalability and provides better visibility into traffic patterns [26].
Every connection from/to every pod in every cluster should be protected.
Keep in mind that sequential iptables rules in multi-cloud setups can add 0.25–0.5 microseconds of latency per rule. To minimize CPU overhead, group multiple rules into a single policy [26]. Using a single global network policy for cluster-wide enforcement is far more efficient than managing numerous individual namespaced policies [26]. These strategies lay the groundwork for effective monitoring and enforcement.
Start by implementing a "Global Default Deny" policy to ensure that only explicitly authorized traffic is allowed [26]. This zero-trust approach ensures that unprotected workloads cannot communicate, requiring intentional connections for every traffic flow.
Before deploying new policies, test them in a staging or audit mode. This step allows you to monitor the impact without disrupting traffic [26]. Tools that provide policy impact previews can help you visualize changes and avoid hours of troubleshooting caused by unforeseen issues.
For real-time visibility, integrate your policy controllers with tools like Splunk for SIEM or notification systems like PagerDuty and Slack [2]. These integrations provide immediate alerts for policy violations or unusual traffic patterns. When setting up these tools, avoid using "all()" selectors in global policies unless absolutely necessary. Doing so can force the data plane to process unnecessary rules, wasting CPU and memory resources [26].
In high-throughput environments, performance optimization is critical. Single-pass pipelined architectures in security gateways help maintain low latency during deep packet inspections. Meanwhile, model-driven frameworks can translate logical configurations into practical, physical settings across your infrastructure [2][8]. Striking the right balance between security and efficiency is vital - use forwarding mode for maximum throughput and proxy mode for deeper inspection when needed.
Once monitoring and enforcement tools are in place, adapting to regulatory changes becomes a more streamlined process.
Regulatory requirements are always changing, and your policy framework needs to keep pace. By using a Policy-as-Code approach, compliance rules can be treated like software - version-controlled, tested, and quickly deployed across multi-cloud environments [24][25]. For example, when new regulations like updated PCI-DSS standards or data residency rules emerge, you can adjust the policy logic once and distribute the changes automatically.
To introduce new regulatory requirements, follow a policy lifecycle that includes preview, staging, and deployment phases [26]. Deploy policies in "audit" or "dry-run" mode first to identify potential violations without blocking legitimate traffic. This lets you assess the impact and gives application teams time to address any issues before enforcement begins.
Continuous compliance monitoring is vital for staying aligned with industry standards. Tools that track real-time compliance against frameworks like CIS Benchmarks, NIST, PCI-DSS, and GDPR can help you spot and fix issues before they escalate [5]. Automating the remediation of violations ensures your infrastructure remains aligned with evolving standards without requiring manual intervention [24].
Centralization doesn't mean consolidation onto one platform. Instead, it means having one place to see, manage, and optimize your cloud operations - regardless of where your workloads run.
Integrate governance checks into your CI/CD pipelines to catch compliance issues during the build process, before they reach production [26]. This "shift-left" approach reduces risk and speeds up remediation. For organizations operating in multi-cloud environments, establishing a unified control layer can standardize performance metrics and security policies across providers like AWS, Azure, and GCP. This eliminates silos and simplifies compliance tracking [24][5].
Manually managing multi-cloud networks is no longer practical as organizations expand across platforms like AWS, Azure, and others. Policy-driven automation offers a solution by shifting from reactive troubleshooting to proactive prevention of misconfigurations [1]. With automation, production VPC deployments can achieve response times in under a second, compared to the hours manual management often requires [1]. Moreover, companies adopting multi-cloud strategies have reported revenue increases of up to 15% and profit gains of 21%, largely due to reduced infrastructure costs [27].
But it’s not just about speed. Automation also strengthens security and boosts resilience. Organizations gain consistent protection across diverse environments, and 82% of businesses using multi-cloud architectures feel more prepared for disaster recovery scenarios [27]. On top of that, identity-focused security models are replacing outdated IP-based systems, aligning with Zero Trust principles - a must-have for today’s dynamic cloud setups [6].
Industry experts echo this shift in security priorities:
A key paradigm shift in ZTAs is the change in focus from security controls based on segmentation and isolation using network parameters (e.g., IP addresses, subnets, perimeter) to identities.
- Ramaswamy Chandramouli and Zack Butcher, NIST [6]
To fully realize these benefits, organizations need to follow proven best practices. Standardized tagging, automated audits, and centralized observability are critical steps. Leveraging Infrastructure as Code and containerization allows workloads to move seamlessly between clouds, optimizing for performance and cost while enhancing flexibility and resilience [5]. These strategies set the stage for operational efficiency and competitive advantages.
The transition to policy-driven automation isn’t just a trend - it’s becoming the norm. With 95% of digital workloads expected to run on cloud-native platforms by 2025 [3], early adopters of automation will gain the upper hand. They’ll enjoy stronger security, lower operational costs, and the agility to adapt quickly to evolving business demands. By starting small - tracking compliance scores and response times - organizations can scale automation gradually, turning fragmented operations into streamlined, unified systems.
Policy-driven automation plays a key role in boosting security across multi-cloud networks by applying uniform policies throughout all environments. This approach minimizes the chances of human error and helps ensure adherence to established security standards.
Automated systems with real-time responsiveness can address new threats as they arise, deploying updates and managing risks without hesitation. This continuous feedback loop strengthens the consistency and dependability of security measures, allowing businesses to safeguard their cloud infrastructure effectively.
Automation in multi-cloud environments offers a smart way to cut costs by ensuring resources are used only when necessary. For instance, dynamic scaling adjusts capacity based on demand, preventing over-provisioning during slower periods. This approach can slash operational expenses by as much as 30–40%. On top of that, spot-pricing options - which take advantage of unused capacity - can deliver discounts of up to 90%, transforming idle resources into budget-friendly solutions.
Another major advantage of automation is its ability to reduce labor costs and minimize errors. Tools like Infrastructure-as-Code (IaC) make deployments faster and more consistent, shrinking provisioning times from days to just minutes. By automating tasks such as network policy management and IP address allocation, businesses can simplify their workflows, speed up application onboarding, and save even more money.
With SurferCloud’s multi-cloud networking suite, these automation features are built right in. This means organizations can efficiently manage costs across all regions while still maintaining top-notch security and performance.
Intent-based networking shifts the focus to high-level business objectives or "intents", which are automatically converted into actionable network configurations. This eliminates the tedious process of manually configuring each device, a hallmark of traditional network management.
With automation at its core, this approach ensures policies are consistently validated and enforced. The result? A network that stays aligned with business goals, minimizes human error, and operates more efficiently.
Selecting the right cloud hosting provider is essential...

Cost Savings: AI predicts failures, saving up to $50 bi...
What Is Web3.0? Web3.0—also known as the Decentral...