UNAT
NAT Gateway is an enterprise-level VPC public network gateway, which allows cloud resources in the subnet that have not been bound to elastic IPs to access the external network. It can also configure port forwarding rules to enable cloud resources to provide services externally.
Create NAT Gateway
Log in to the console, select "Private Network VPC" in [Products and Services], enter the private network page, and select the NAT Gateway tab.
Click 'Create NAT Gateway' to open a new window.

In the new window, select VPC and subnet, choose 'Normal Mode' for the outbound mode, select the public IP, bandwidth, and firewall required for the NAT gateway, then click 'OK'.
After creation, you can see the information of the NAT gateway in the list.
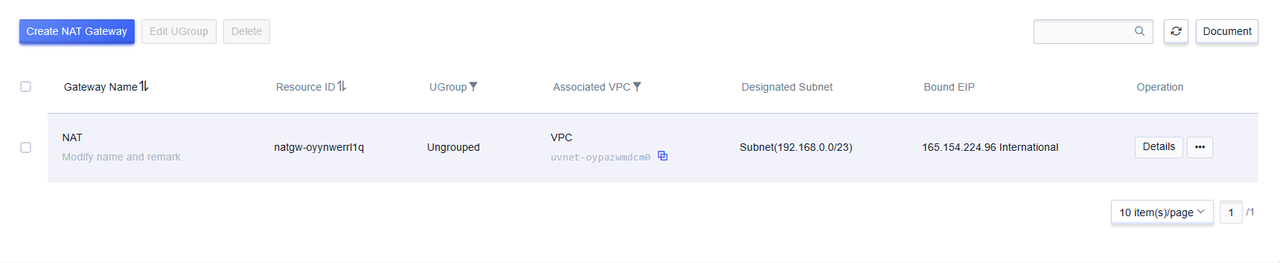
After the NAT gateway is created, cloud resources in the specified subnet that are not bound to an elastic IP can access the internet through the NAT gateway.
Whitelist Mode
The NAT gateway also offers a whitelist mode.
In whitelist mode, only cloud resources that are in the specified subnet of the NAT gateway and defined in the whitelist can access the internet through this NAT gateway.
- When creating a NAT gateway, except for selecting 'whitelist mode', the rest is the same as 'normal mode'.
- The whitelist of a newly created NAT gateway is empty, no cloud resources can access the internet, you need to configure the whitelist. Click the 'Mode Management' button in the list to enter the NAT gateway details page.

Click on the 'Mode Management' tab to enter the whitelist management.

Click 'Add to Whitelist' to add the desired main resources.
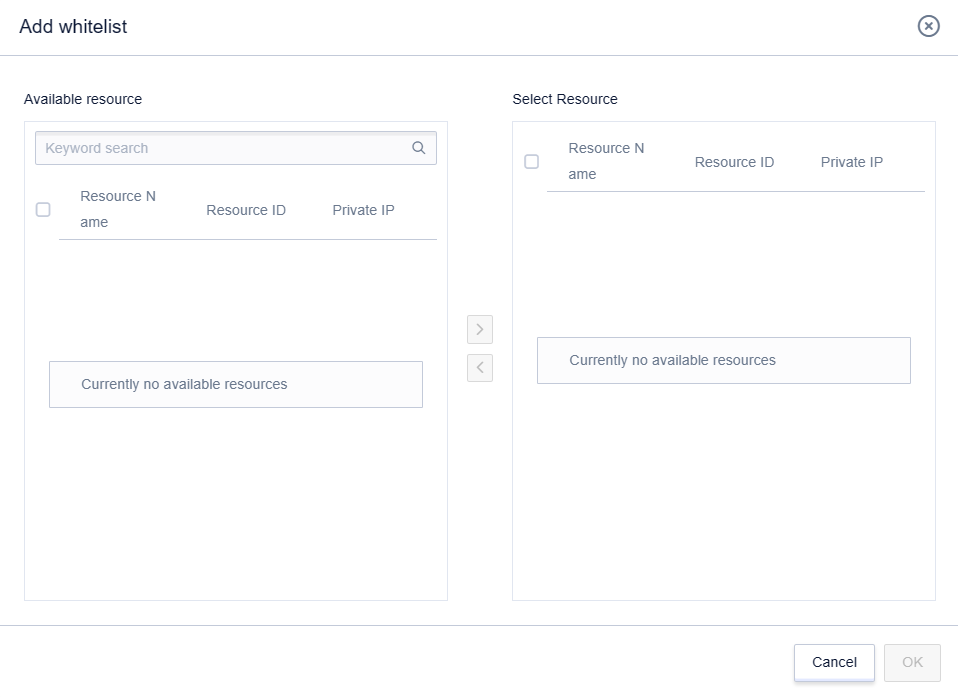
After clicking 'Confirm', the list will take effect, and cloud resources in the whitelist can access the internet.
Port Forwarding
Configuring port forwarding allows a specific port of a cloud resource to be accessed by the external network, in order to provide services or for management.
On the NAT gateway details page, switch to the 'Port Forwarding' tab.
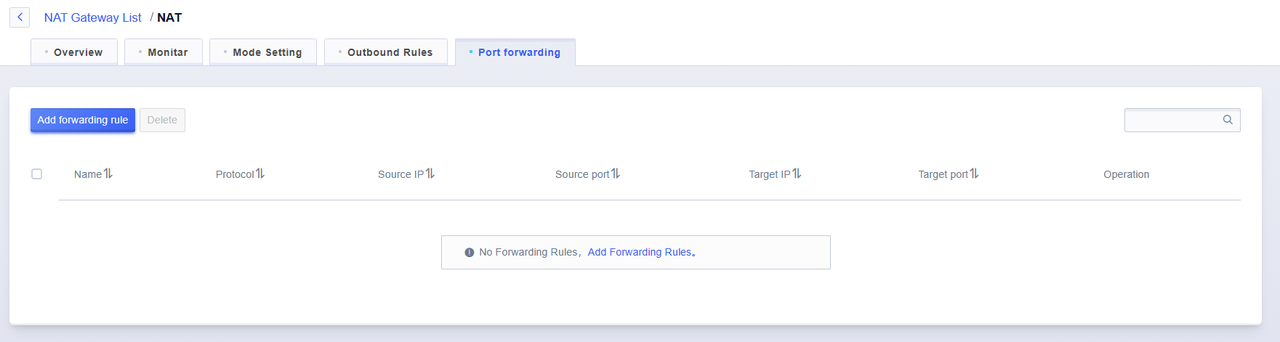
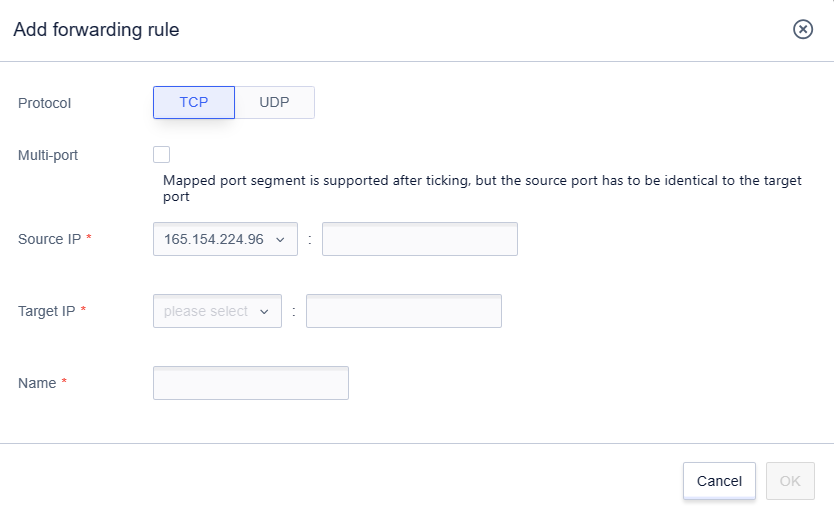
Click 'Add Forwarding Rule' to add a new rule.
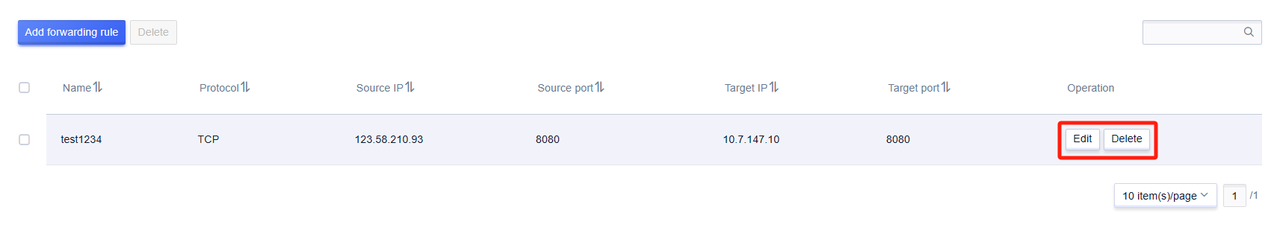
Click the 'Modify' button to modify existing rules.
Click the 'Delete' button to delete existing rules.
Export Rules
Configure the network exit, you can specify an elastic IP for a single cloud resource in the subnet to access the external network through the NAT gateway, or you can specify all cloud resources to access the external network through load balancing or fixed EIP.
On the NAT gateway details page, switch to the 'Exit Rules' tab, and in the 'Exit Rules' module, you can manage the elastic IP bound to the NAT gateway.

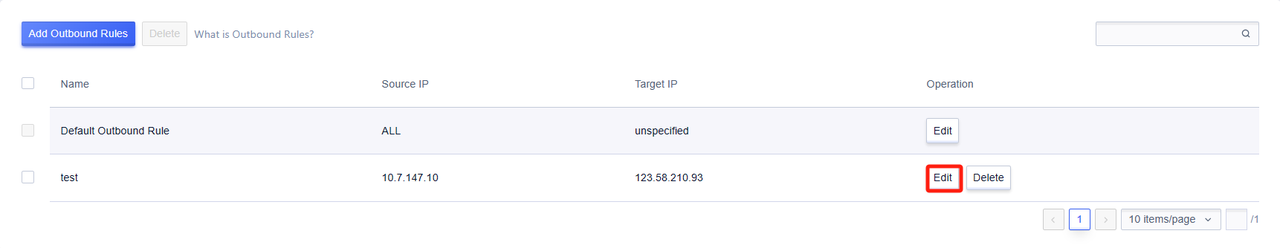
- A 'Default Outbound Rule' exists by default, which is used to record the default outbound of this NAT gateway. It can be modified through the 'Edit' button, but cannot be deleted. The priority of the Default Outbound Rule is the lowest.
- When the NAT default outbound rule is set to load balancing mode, the outbound traffic will be allocated according to the hash algorithm. Updating EIP does not affect the existing connections, and new connections will be evenly distributed according to the current number of EIPs.
Click the 'Edit' button to add outbound rules, and specify the outbound for a single cloud resource.
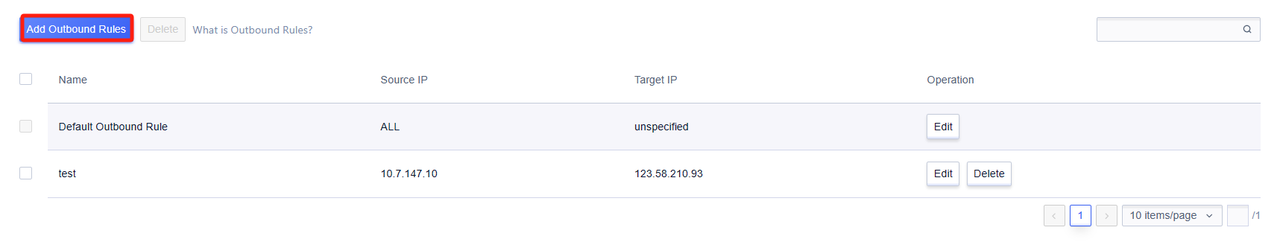
After successful addition, the rules can be modified. Among them, the default rule can modify the target IP, that is, the exit IP. Other exit rules can modify the name and target IP.